Secure IoT Device Access: Best Practices & Solutions [2024]
In an era where the Internet of Things (IoT) has become ubiquitous, from smart homes to industrial automation, the persistent question is: Are our connected devices truly secure? The answer, often unsettling, is that every connection introduces a new layer of vulnerability, demanding a proactive approach to cybersecurity.
The expansion of IoT has revolutionized our lives, offering unprecedented levels of convenience and efficiency. However, this convenience comes at a cost. Every time a device connects to the internet whether it's a sophisticated piece of machinery in a factory, a smart security camera monitoring your property, or a simple laptop a series of security concerns immediately come to the forefront. The potential for data breaches, unauthorized access, and malicious attacks is ever-present, turning our interconnected world into a landscape of potential threats.
| Category | Details |
| Definition: | IoT (Internet of Things) Remote Access: The practice of securely connecting to and managing IoT devices from a remote location. |
| Importance: | Enables troubleshooting, configuration updates, data monitoring, and control of IoT devices deployed in various settings, including those behind firewalls or in remote locations. |
| Key Technologies: |
|
| Key Considerations: |
|
| Methods of Access: |
|
| Security Benefits: |
|
| References: | AWS IoT Device Management |
Consider the ramifications: these connected devices, whether residing in the office, at home, or utilized in both environments, inherently carry a risk. Corporate secrets, personal data, and operational information can be exposed, potentially leading to significant financial and reputational damage. This is where the strategies for securing these devices come into play.
- Melissa Rauch Naked Pics A Closer Look At The Rumors And Facts
- Aditi Mistry Neud Video A Comprehensive Look Into The Viral Sensation
One of the most effective methods for securing remote access to IoT devices is through the utilization of a Virtual Private Network (VPN). VPNs create a secure, encrypted connection between your device and the network where the IoT device is located. This allows you to access your device as if you were on the same local network, effectively masking your IP address and encrypting your data, providing a critical layer of security, especially when dealing with devices behind firewalls or on private networks.
In more complex environments, such as professional or industrial settings, the need for robust security measures escalates. These settings often deal with sensitive data or necessitate direct remote access for tasks like troubleshooting, configuration updates, and other operational needs. In these scenarios, the use of VPNs becomes even more critical, alongside other security protocols.
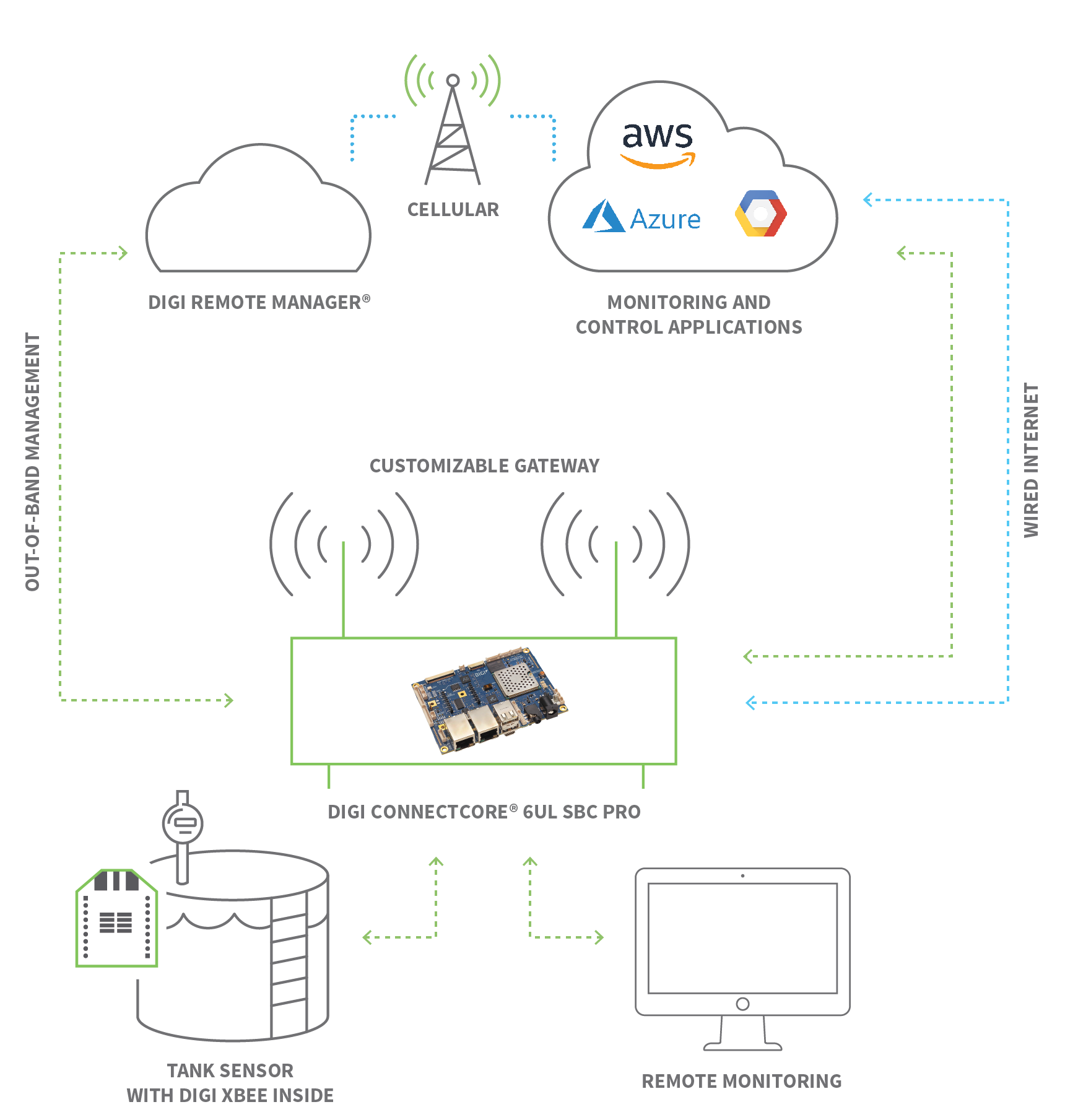
When devices are deployed in remote locations, often behind stringent firewalls, the challenge of accessing these devices for maintenance and updates becomes significant. This is where solutions like secure tunneling come to the fore. Secure tunneling, a feature offered by AWS IoT Device Management, has been instrumental in helping customers remotely manage their devices. This allows for remote configuration and operational tasks, streamlining processes and reducing downtime.
- Raspberry Pi Remote Your Ultimate Guide To Setting Up And Mastering Remote Access
- Movierulz In Kannada Your Ultimate Guide To Kannada Movies Online
To further enhance the capabilities of device management, integrating secure IoT device remote access solutions, such as TeamViewer Tensor, can be advantageous. These tools enable users to manage and troubleshoot problems with their remote IoT devices from anywhere, at any time. This functionality is crucial for organizations that rely on constant connectivity and up-time of their devices.
The impact of IoT on consumer interactions is undeniable, reshaping how we interact with technology. IoT offers unparalleled control and optimization, driving efficiency at the edge of the enterprise and redefining customer experiences. This shift towards decentralized control, however, necessitates a heightened focus on security. As IoT devices become more prevalent, the importance of securing them becomes paramount.
A crucial practice in maintaining a secure IoT environment is to regularly audit and, if necessary, eliminate any unused IoT devices. Any device that remains connected to the network but is not actively maintained represents a significant security risk. These dormant devices can act as potential entry points for attackers, providing a gateway to the network's more sensitive components.
A remote IoT platform provides users with the ability to remotely control IoT devices through a web browser, offering a convenient and accessible method for device management. Similarly, setting up a VNC server on a device like a Raspberry Pi allows users to view and interact with the device's desktop from any location with an internet connection. This approach can be highly effective for remote troubleshooting and configuration tasks, improving efficiency and productivity.
To manage IoT devices over the internet effectively and securely, implementing web applications and executing remote commands are essential. This allows for monitoring and control of devices from anywhere, ensuring operational efficiency. Using platforms such as SocketXP can further streamline the process, allowing for secure remote connections to IoT devices located behind NAT routers and firewalls.
Secure tunneling plays a critical role in providing a secure remote access solution, especially when integrated with AWS IoT. This allows for accessing IoT devices remotely from any location. The feature allows the user to remotely manage and interact with their IoT devices, making it simple to resolve issues without needing physical access.
Ensuring secure IoT remote device access involves adhering to several key practices:
- Robust Encryption: Utilizing robust encryption protocols like TLS or DTLS is essential for protecting all network traffic.
- Firewall Configuration: Correctly configuring firewalls to permit only essential traffic is crucial for preventing unauthorized access.
- VPN Usage: Implementing VPN connections for remote access to the IoT network is a fundamental security measure.
IoT devices are designed to provide automation, efficiency, and convenience, but neglecting their security can create vulnerabilities. Prioritizing security measures ensures that these devices remain safe and useful.
For secure remote monitoring and management, IoT remote SSH connections are a perfect solution. Putty provides a GUI window to log in and establish an SSH connection to your devices. For users of Windows and macOS, the guide includes information on how to set up secure connections, including those on AWS IoT instances.
A VPN is a commonly used approach to remotely access an IoT device, creating a secure connection. This facilitates access to the device as if the user were on the same local network.
As we have highlighted, IoT devices offer automation, efficiency, and convenience. However, leaving them unmonitored opens pathways for vulnerability. By using SSH, secure monitoring and remote management become possible. Utilizing applications like Putty provides a GUI window to manage your devices.
Secure tunneling is an excellent method to establish a secure, remote access solution that works seamlessly with AWS IoT, allowing access to devices from any location. This is demonstrated through the management and troubleshooting of remote devices from a web application.
This guide, provides a walk-through to show how to remotely access IoT devices using SSH on various systems. The guide details how to set up a secure connection, including AWS IoT instances. Through a VPN, the user can create a secure network. This enables users to access devices as if they were on a local network.
The connection between services and IoT devices, initiated by the service, uses a device stream session. Implementation always starts with the serviceclient of the service SDK, and utilizes the service connection string. Utilizing the createstreamasync method starts a connection request to an IoT device.
Wired connections offer reliable and secure methods for IoT devices to connect to the internet. They deliver low latency and are protected from interference, but there are downsides such as lack of mobility.
Additionally, for accessing IoT devices, a compatible IoT device and a stable internet connection are needed. Before setting up a Linux server for remote accessing IoT devices, certain prerequisites must be considered.
To connect IoT devices to cloud platforms, the use of provided SDKs and libraries is essential. This requires code to manage communication and data exchange. Once a connection is made, devices can begin sending and receiving data.
SocketXP, provides a method of creating secure reverse SSL/TLS tunnels. These tunnels are useful for exposing applications or services in a private network to customers or vendors. SocketXP addresses security concerns brought about by SSH, unlike other solutions. Restricting access and whitelisting IP addresses, prevents unauthorized access, making SocketXP ideal for many applications.
An IoT device agent, such as the IoT agent snippet, runs on a remote device, connecting it to the AWS IoT device gateway. The device is configured with an MQTT topic subscription. This, alongside the steps outlined previously, helps secure and monitor devices.


Detail Author:
- Name : Mrs. Kaitlin Hettinger IV
- Username : nlittel
- Email : camille97@hotmail.com
- Birthdate : 1993-02-06
- Address : 4272 Miller Brook Apt. 917 Wuckertbury, KY 63563
- Phone : +1-856-260-0110
- Company : Mayert, Bailey and Wunsch
- Job : Jewelry Model OR Mold Makers
- Bio : Consequuntur eos repellendus quam odit. Eos sed esse totam dolore. Quibusdam quia sint vero sequi atque porro culpa reprehenderit.
Socials
instagram:
- url : https://instagram.com/hilld
- username : hilld
- bio : Quia quia quia architecto quia. Et id quos asperiores facere. Eos dolorem nostrum ipsa odit culpa.
- followers : 3435
- following : 651
facebook:
- url : https://facebook.com/hill1989
- username : hill1989
- bio : Omnis atque id et facilis magni.
- followers : 207
- following : 2077
tiktok:
- url : https://tiktok.com/@domenichill
- username : domenichill
- bio : Eum in est iusto dignissimos iure. Sit quaerat quam qui voluptates.
- followers : 1688
- following : 2108
twitter:
- url : https://twitter.com/domenic6257
- username : domenic6257
- bio : Nobis quam ut fuga officia aut incidunt. Est alias fugiat id quae debitis. Necessitatibus praesentium dicta voluptates est.
- followers : 5368
- following : 718