How To Fix Rasplex & Plex Remote Access Problems
Can a sophisticated remote access system be truly secure from unauthorized access? The persistent vulnerabilities and evolving threat landscape demand constant vigilance and proactive security measures.
We often hear about the complexities of implementing and maintaining remote access, the different methods and their impacts on desktop operation and security which are accessible to everyone.
| Aspect | Details |
|---|---|
| Name | Not Applicable |
| Date of Birth | Not Applicable |
| Place of Birth | Not Applicable |
| Education | Not Applicable |
| Career | Not Applicable |
| Professional Information | Not Applicable |
The allure of convenient remote access has drawn many people to conceal their computer at a single point, which can't be viewed for several days. This is because the remote access point configuration is often set up using the 'Rasplex' configuration.
- Unveiling The Truth Hot Sex Aditi Live Ndash What You Need To Know
- Aditi Mistry Latest Hot Live The Rising Star Of Bollywood
Many remote access solutions are intended to provide the ability to control and see desktop functions. Many people often use the remote desktop program to control things. It's very useful and this is possible to do for all.
One Rasplex is running now, it provides the ability to share all of the media.
Configuring Rasplex is the process of taking care of remote access.
- Aditimistry New Live Video A Deep Dive Into The World Of Digital Magic
- Movierulz In Kannada Your Ultimate Guide To Kannada Movies Online
Hello friends, welcome to the tutorial, It's an amazing aspect, which offers many useful things, like easy access and better configuration.
Rasplex is very helpful for use with your devices.
Remote Access Plus is a great solution. It is a great option for anyone who needs it. I was impressed with it.
DIY remote infrastructure for remote access, and for data gathering, can be very helpful.
In this configuration, you can set up your private remote access.
Here's a more detailed exploration of these points, ensuring a unique and engaging narrative:
The world of remote access is vast and varied, a constantly evolving landscape shaped by technological advancements, shifting user needs, and, unfortunately, the persistent threat of malicious actors. The core concept the ability to connect to a system or network from a distant location seems simple enough. Yet, the practicalities of achieving secure and reliable remote access are anything but. This article delves into the intricacies of remote access, examining the challenges, exploring the solutions, and offering insights to help you navigate this complex domain.
One of the most significant challenges in the realm of remote access is the inherent tension between convenience and security. Making it easy for authorized users to connect often means creating potential vulnerabilities that could be exploited by those with ill intent. This trade-off demands a thoughtful and multi-layered approach to security, incorporating measures such as strong authentication, encryption, and intrusion detection systems.
The methods for achieving remote access are as diverse as the needs of those who utilize them. Virtual Private Networks (VPNs) have long been a cornerstone of secure remote connectivity, creating an encrypted tunnel between the user's device and the network. However, even VPNs are not immune to security concerns, and the specific implementation and configuration can significantly impact their effectiveness.
Remote Desktop Protocol (RDP) and similar technologies provide direct access to a remote computer's graphical interface. While offering a seamless user experience, these protocols can be susceptible to brute-force attacks and other vulnerabilities if not properly secured. Careful attention to access controls, regular patching, and the use of strong passwords are essential.
Cloud-based remote access solutions have gained popularity, offering scalability, ease of management, and often, enhanced security features. These platforms typically rely on secure protocols and robust infrastructure, but it is crucial to choose providers with a strong track record and a commitment to security best practices.
Beyond the technical aspects, effective remote access also requires robust policies and procedures. Clear guidelines on acceptable use, password management, and data security are crucial. Regular security audits and user training are also vital to maintain a strong security posture.
The evolving threat landscape further complicates the task of securing remote access. Cybercriminals are constantly developing new techniques and exploiting vulnerabilities. Staying ahead of these threats requires continuous monitoring, threat intelligence gathering, and proactive security measures. This includes:
Multi-Factor Authentication (MFA): Implementing MFA adds an extra layer of security by requiring users to verify their identity through multiple methods, such as a password and a one-time code from a mobile device.
Regular Security Audits and Penetration Testing: These assessments help identify vulnerabilities and weaknesses in the remote access infrastructure. Regular testing ensures that the system is capable and that the system is secure.
Endpoint Security: Protecting the devices used for remote access is essential. This includes the installation of antivirus software, firewalls, and other security tools, as well as policies that limit access to sensitive data from unsecured devices.
Network Segmentation: Dividing the network into segments can limit the impact of a security breach. If an attacker gains access to a remote access system, they will be restricted in their ability to move laterally within the network.
User Education: Users are often the weakest link in the security chain. Providing them with proper education about security threats and best practices can significantly reduce the risk of a security breach.
Data encryption: all data should be encrypted during transfer and at rest to maintain the confidentiality of information.
A secure system for remote access is not something to be created and then ignored. It is a dynamic, living system that requires constant attention, and a dedication to the task. Keeping these practices in mind, you can make remote access safe and useful.
As organizations embrace remote work and the need for anywhere, anytime access to resources, the importance of strong and secure remote access solutions will only continue to grow. It is a challenge that demands a multi-faceted approach, encompassing technology, policy, and user awareness. By understanding the intricacies of this domain, you can build a secure and productive remote access environment that supports your business goals while mitigating the ever-present risk of cyber threats.
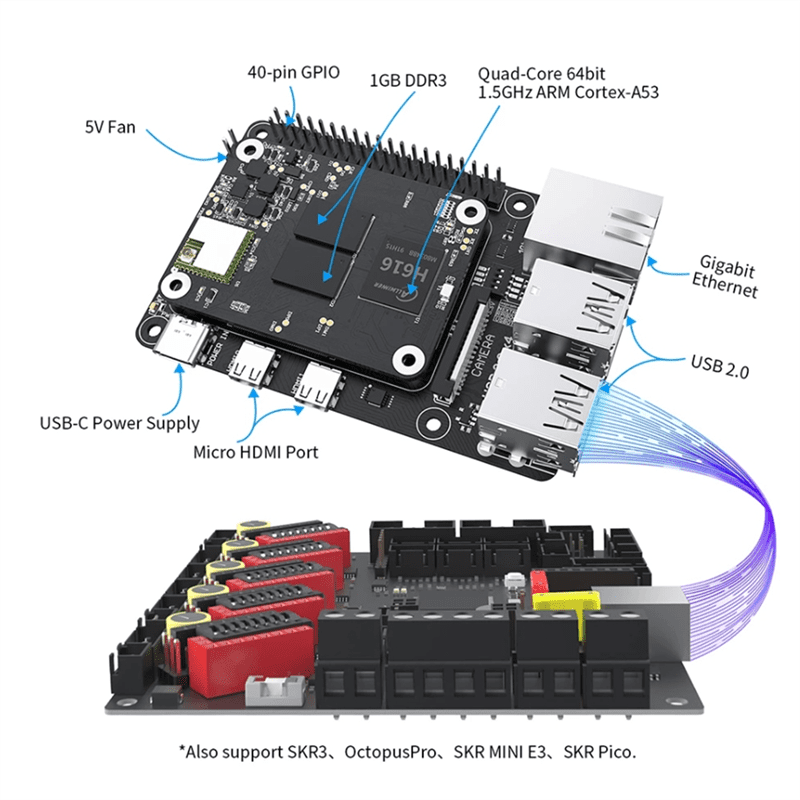

Detail Author:
- Name : Tristin Ortiz III
- Username : mitchell.abshire
- Email : piper.king@hotmail.com
- Birthdate : 2004-09-18
- Address : 523 Cassin Parks Apt. 637 Richmondton, SC 39151
- Phone : (541) 462-5814
- Company : Purdy, Bahringer and Gislason
- Job : Paving Equipment Operator
- Bio : Quas voluptates rerum rem repellat blanditiis est. Fugit et dolores fugiat quasi eum. Dolorem libero fuga omnis magni. Magni eum suscipit quos assumenda debitis.
Socials
twitter:
- url : https://twitter.com/rosalindkulas
- username : rosalindkulas
- bio : Sunt necessitatibus consequatur fugit quibusdam ut. Non adipisci dolorem quos cupiditate nulla.
- followers : 5090
- following : 2142
linkedin:
- url : https://linkedin.com/in/kulas1990
- username : kulas1990
- bio : Omnis ullam iste qui ut qui.
- followers : 5987
- following : 1548
facebook:
- url : https://facebook.com/rosalind.kulas
- username : rosalind.kulas
- bio : Maxime in velit fugit iste et eligendi quod.
- followers : 5176
- following : 1729
tiktok:
- url : https://tiktok.com/@rosalind.kulas
- username : rosalind.kulas
- bio : Molestiae eaque similique ut quo aspernatur placeat dignissimos.
- followers : 4021
- following : 1993